Making The CIA Triad Applicable
Essential Cybersecurity Principles for Protecting Your Data in the Digital Age
Introduction
When your incident response team sends an alert that your proactive threat detection system has spotted malware, you dive in and take action to neutralize the threat. Cybersecurity is the practice of protecting people, data, systems, and networks from attacks. In order to do this security professionals begin by utilizing a concept known as the CIA Triad, which was briefly discussed in our article “Cybersecurity Fundamentals: A Guide for Non-Technical Leaders”. In this article, we’ll delve deeper into the CIA Triad. By the end, you’ll grasp why, regardless of your role—business executive, startup owner, or remote worker—the CIA Triad is a crucial concept to grasp.
Background
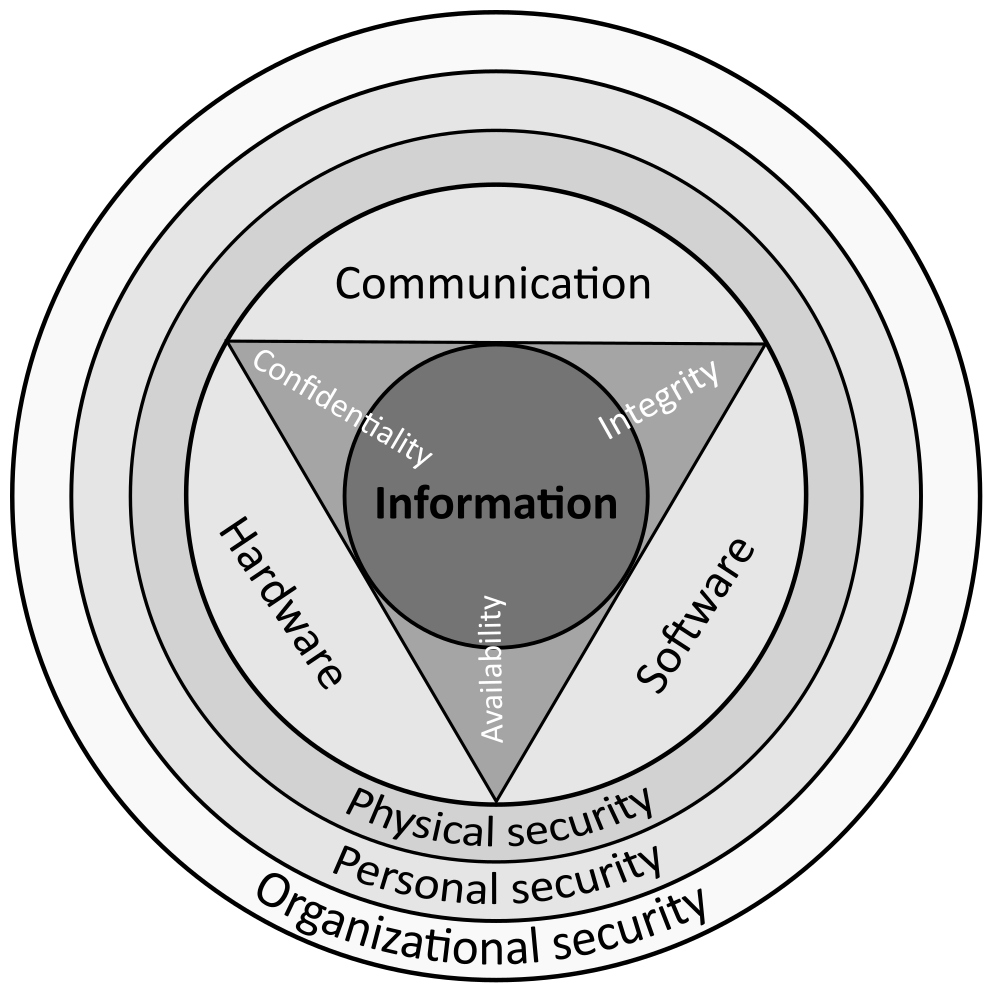
There are many sources attributed to the concepts of confidentiality, integrity, availability when it comes to their usage and origin. Many of these concepts began in the U.S. military through the late 1970s and 1980s however the exact origin of the term ‘CIA Triad’ is unknown. This acronym however provides the fundamental basis of information security concepts, where theoretically data sits in the middle of the triangle formed by the three concepts. Overtime as threats have grown, additional layers have been added to the triad to include concepts like authenticity, non-repudiation, and accountability. Today security professionals from a wide range of backgrounds have different opinions on the CIA and its usefulness when it comes to the current threat landscape we face. However, for anyone who is trying to understand what cybersecurity is and how you begin going about protecting your data, the CIA Triad remains an invaluable and fundamental starting point.
Confidentiality
Confidentiality is basically defined as only authorized individuals have access to the data. A loss of confidentiality would be some form of unauthorized disclosure of information. As data/information is crucial in modern day business and business processes, confidentiality remains the primary focus of security efforts. For example, let’s say that during a routine audit, the auditor discovers that unauthorized access to your internal data repository has been occurring for several months. A hacker exploited a vulnerability in your outdated firewall to gain access to confidential client information, including personally identifiable information records from several of your highest paying clients. This would be a potentially catastrophic loss of confidentiality. Maybe you’re still using paper records instead of electronic, but you don’t shred documentation before disposal. Dumpster diving is another form of a loss of confidentiality that could potentially open you to outside risk. To protect against the various ways of confidentiality loss you can implement things like a clean desk policy. Adding layers of rules and encryption can help to provide more defense to limit what a potential hacker can exploit. Of course, above all else, user education around cybersecurity for you and your employees will always pay off in the long run especially when it comes to recognizing social engineering attacks.
Integrity
The definition of integrity in cybersecurity revolves around preventing unauthorized changes to information. This means it is the responsibility of the security professional to guard against intentional alterations by attackers or disruptions. Now when we are talking about the specific types of attacks and their outcomes, we are not talking about a disruption preventing access to a specific system. A loss of integrity is the unauthorized modification or destruction of information. An impersonation attack occurs when a hacker poses as a trusted individual, like a CEO, to manipulate employees into sharing sensitive information. For example, a hacker deceives the finance team with a fake email, gaining unauthorized access to confidential data and diverting company funds because the team believes it to be coming from the CEO.
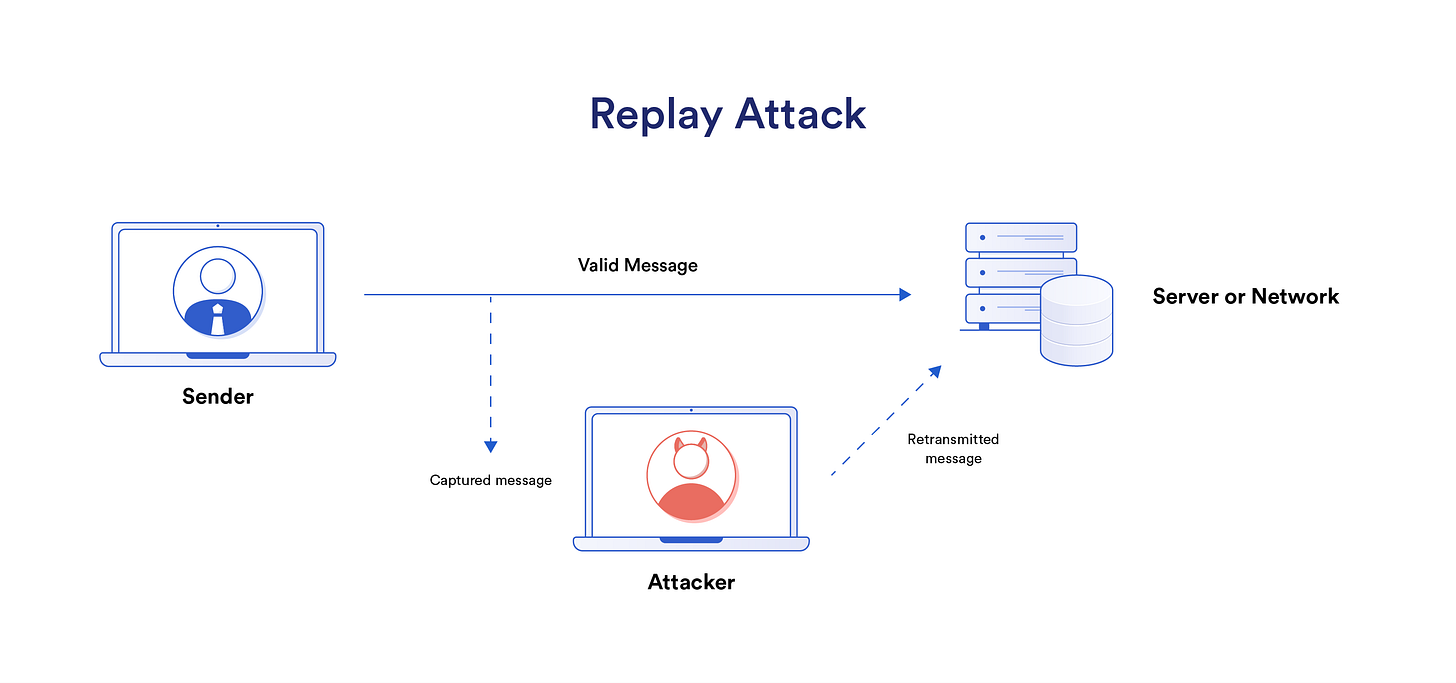
Another type of attack you might see against integrity is known as a replay attack. A replay attack is a sneaky cyber trick where a bad actor sneaks into a legitimate data stream and copies it. Then, they play the copied data back to the system, tricking it into doing things it wasn’t supposed to do. This can let the attacker do things they shouldn’t be able to, like access sensitive information or take over the system. We work to prevent these types of attacks using controls like encrypting data in transit and at rest. Implement the Principle of Least Privilege, which states that people should only have the access they need to do their jobs, not more. User education in learning how to spot potential malicious and fake emails is highly important to preventing a loss of integrity.
Availability
Making sure that information and information systems are available to authorized users when they need it is the basis of the availability branch in the triad. A loss of availability occurs when there is disruption of access to or use of information or an information system and hence its importance as the vital 3rd element in the triad. The most common form of attacks associated with a loss of availability are Denial-of-Service attacks. Let’s say you’re a financial service startup whose online banking platform is suddenly targeted with a surge of illegitimate traffic. Suddenly customers can’t get access to their accounts as the system slows and eventually becomes completely inaccessible causing widespread concern among consumers and you’re already stretched IT department. The consequences in this scenario could be devastating to your reputation and could cause unforeseen financial repercussions down the line. To prevent loss of availability we look to utilize resources such as redundant power systems, build redundancy into systems and hardware to compensate for potential component failures, backup data centers in remote locations or the cloud. Implementing firewalls and working with your Internet Service Provider to block illegitimate requests is key in this situation to getting your systems back online and preventing these types of attacks.
What next?
You now have a fundamental knowledge of what information security is and where you start when you go about thinking about protecting data that is important to you or your organization. What’s even better is you can now take this knowledge and apply it one step further in correlation with the NIST RMF via FIPS PUB 199 to understand how you may begin categorizing the importance of your data at rest or in transit, information systems, business processes, etc. You can derive value from implementing security controls based upon what you perceive as your crown jewels, and what is not worth protecting. If you would like to know more about the Risk Management Frame work check out our Substack article “Simplify The Framework”, where we go into a little more detail of the NIST RMF concepts. If you haven’t before, be sure to read “Cybersecurity Fundamentals: A Guide for Non-Technical Leaders” as it continues the discussion of cybersecurity in-depth. In the future we will discuss a more advanced framework called the Diamond Model, a tool for analyzing cyber intrusions.