Cybersecurity Fundamentals: A Guide for Non-Technical Leaders
Master the Basics of Cybersecurity to Safeguard Your Business and Build Trust
Introduction
Are you a healthcare, financial, or tech professional looking to enhance your organization's cybersecurity but unsure where to start? You're not alone. Many individuals without a technical background find themselves overwhelmed by the complex terminology and concepts. Protecting your customers' data, intellectual property, and employees is crucial, but the first step can be challenging.
In this article, we'll simplify the essential concepts of cybersecurity, providing you with a practical starting point tailored to your organization's needs. By the end, you'll gain the confidence and knowledge to begin implementing effective security measures, setting you apart from competitors who haven't yet accessed these insights.
Basics to Understand
Regulations, Laws, and Standards
In my previous article,
I discussed the three major laws, regulations, and standards businesses commonly encounter, along with the challenges of compliance. Understanding the specific laws, regulations, and standards applicable to your organization is crucial for setting priorities. This is particularly important if your operations span multiple states, as differing state and federal laws can raise jurisdictional questions. For instance, regulations like PCI DSS are self-regulatory and apply globally to credit card transactions. The next step is to grasp how policies, standards, guidelines, and procedures integrate with your compliance efforts.
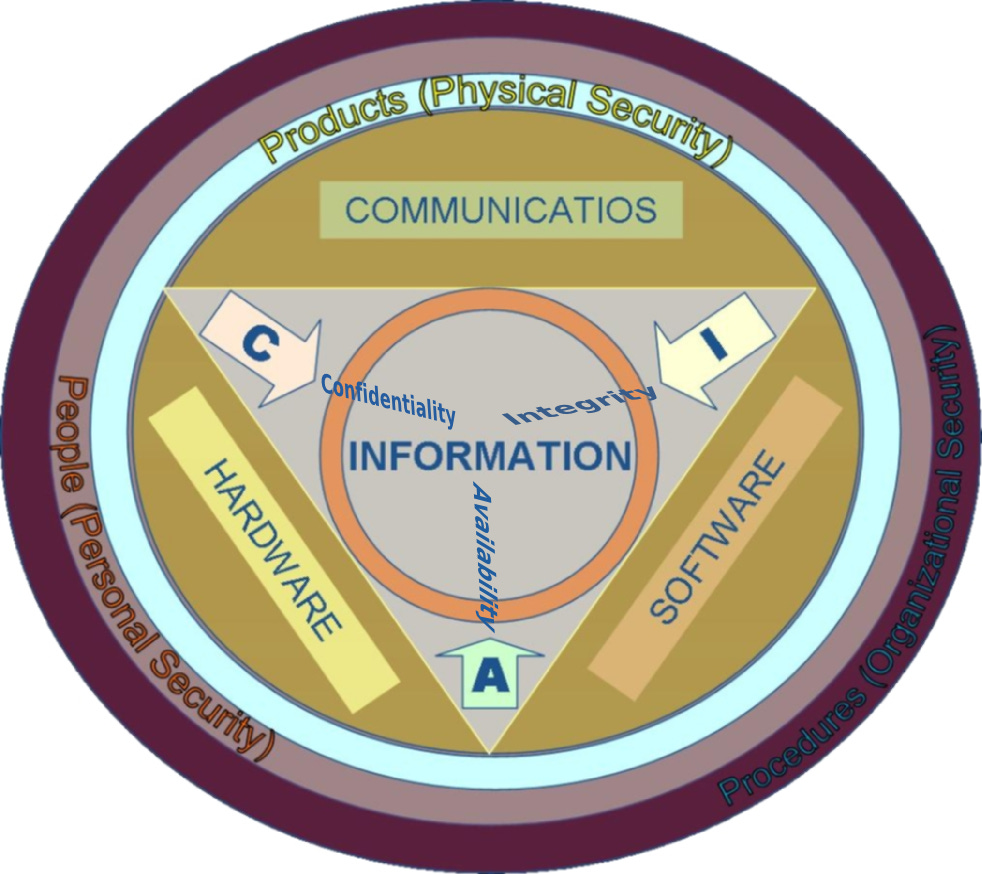
Understanding the CIA Triad
The CIA Triad—Confidentiality, Integrity, and Availability—represents the primary objectives of cybersecurity within an organization. In today's digital landscape, information is vital to business operations. Confidentiality ensures that only authorized individuals can access sensitive information, making it a core focus of information security. Integrity safeguards data against unauthorized changes, protecting it from intentional alterations and accidental disruptions. Availability guarantees that business processes and data remain accessible to authorized users when needed. There are more layers, but grasping these main concepts is essential for effective cybersecurity efforts.
Understanding the Cyber Kill Chain
Introduced by the Lockheed Martin Cyber Emergency Response Team in 2009, the Cyber Kill Chain framework breaks down cyber attacks into seven distinct stages, enhancing our ability to understand and counter them effectively. These stages are:
Reconnaissance
Weaponization
Delivery
Exploitation
Installation
Command and Control
Action
This structured approach aids in analyzing and defending against cyber threats. Attackers weaponize vulnerabilities tailored to specific targets, deliver them through methods like phishing or compromised websites, exploit them to install malware and establish access, and use command and control to direct remote actions, culminating in an action that typically harms the target. Attackers' motives can range from activism to financial gain, but they all exploit vulnerabilities in interconnected systems, underscoring the necessity for robust cybersecurity measures.
Security Is a Top Priority
In today's complex threat landscape, which evolves continuously and grows more aggressive and sophisticated with each passing day, adopting a proactive mindset over a reactive one is crucial for an effective security plan. By hiring an ethical hacker to test your systems and networks, you can identify and address vulnerabilities before they become actual incidents, saving your business money, time, and stress in the long run.
From the onset, incorporate safeguards into your security privacy plan. Understanding the differences between administrative, physical, and technical controls and knowing the correct way to implement them, is the most cost-effective way to layer your defenses. Remember, securing an organization’s information systems and processes is everyone’s responsibility. By fostering a security-conscious culture, you empower every member of your organization to play a critical role in safeguarding sensitive information.
Understanding Cybersecurity Threats and Vulnerabilities
Once you've grasped the basics of cybersecurity, the next step is to explore the threat landscape and how to navigate it effectively. For healthcare and tech professionals like yourself, understanding two main types of cyber attacks is crucial, Passive Attacks and Active Attacks.
Our cybersecurity risk arises from a combination of external threats and internal vulnerabilities within our systems and processes. Effective countermeasures, or controls, are essential to mitigate these risks. At its core, cybersecurity is about managing the risks associated with operating in a connected world.
By staying informed and proactive, you can protect your practice or company from evolving cyber threats. Remember, ongoing vigilance and regular updates to your security measures are key to maintaining robust cybersecurity.
Understanding Passive Cyber Attacks
Passive attacks are often among the first and most common threats faced by networks in both healthcare and tech industries. These silent intrusions come in two main forms:
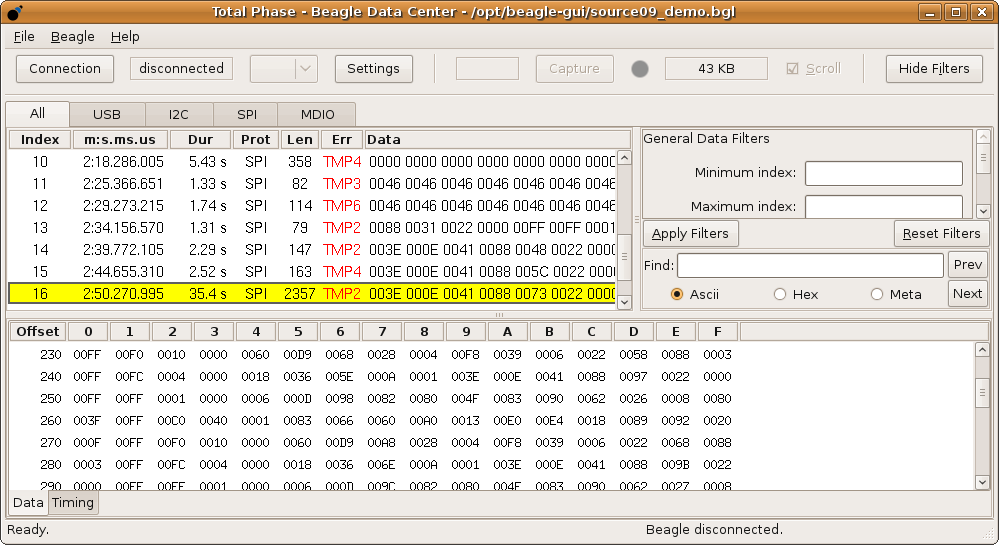
Traffic Sniffing: This involves intercepting data packets as they travel across your network, allowing attackers to gather sensitive information without direct interaction.
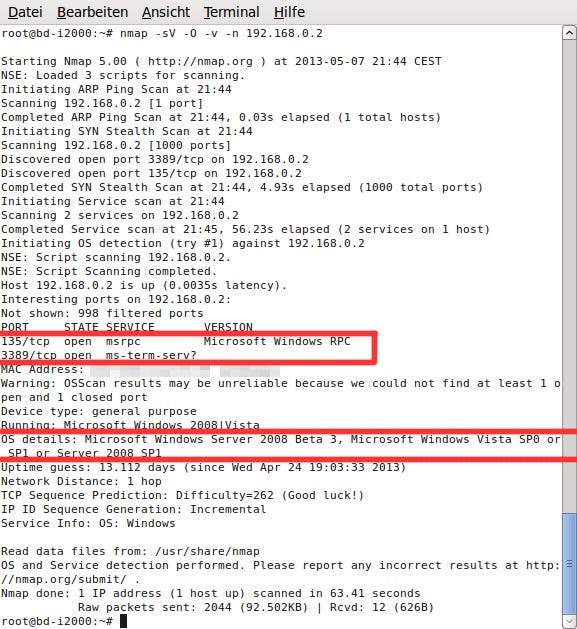
Port Scanning: Slightly more intrusive, this method involves probing open ports on network devices to identify vulnerabilities that could be exploited in future attacks.
Understanding these passive attack strategies is crucial for identifying and addressing potential weaknesses in your organization's network. By implementing robust security measures and monitoring network activity, you can protect against these common vulnerabilities and safeguard your sensitive data.
Understanding Active Cyber Attacks
Active attacks typically follow the initial reconnaissance gained from passive attacks. With detailed information about your systems and applications, attackers can craft and deploy malware to infiltrate and spread across your network. However, direct malware deployment isn't always their primary goal.
Consider the incident in March 2013 involving CyberBunker, a Dutch internet provider. After being blacklisted by Spamhaus—a list identifying spam sources—CyberBunker launched a massive Distributed Denial of Service (DDoS) attack against Spamhaus's DNS servers. This unprecedented assault exploited vulnerabilities in DNS security, aiming to disrupt Spamhaus's operations. It required intervention from major tech companies and international cyber-police to resolve.
This incident underscores how attackers often target business processes with overwhelming cyber assaults, emphasizing the importance of robust cybersecurity measures to protect your network and maintain operational integrity.
Understanding Risk in Cybersecurity
Risk begins with identifying a threat event, which we analyze to assess its likelihood. This involves evaluating the threat actors, their capabilities, resources, and intent. Attackers usually strike when the potential reward—be it financial gain, intelligence gathering, or notoriety—outweighs the cost.
The next step is identifying which of our data processing systems are vulnerable to attacks. Not all vulnerabilities pose the same level of threat, so it's crucial to assess each threat event's potential impact on our processes. Sometimes, securing a process may cost more than the impact itself, leading us to accept a certain level of risk—our risk appetite. Conversely, we might implement controls to protect our systems when the risk of inaction is too significant.
Ultimately, understanding and managing risk determines how effectively a business can achieve its cybersecurity goals, ensuring the protection of critical systems and data.
Implementing Effective Cybersecurity Controls
In cybersecurity, controls are essential tools combining policies, processes, and technical solutions to mitigate risks identified through threat intelligence and risk assessments. A crucial strategy is employing multiple defense methods within your organization, known as defense in depth, to thwart potential attacks. Network administrators implement various security controls to fortify computer infrastructure, including firewalls, spam filters, and VLANs. However, the most critical control involves educating people about their role in data protection. Empowering your team with the knowledge and skills to safeguard information is key to a robust cybersecurity posture.
Simplify Your Security Approach
This guide offers a clear overview of essential cybersecurity concepts, empowering you to understand key terms. At Sudo Truth, we're committed to supporting your organization's security goals. If you found this guide helpful, follow us on Bluesky for more updates. For in-depth tips and resources, consider our paid Substack subscription. Our aim is to enhance your security efficiently and cost-effectively. A secure business fosters trust and attracts customers who prioritize safety. Together, let's build a more secure world, one byte at a time!